Your cart is currently empty!
Stop Sniffing Me
So I am constantly learning. 40% of the internet is using the WordPress platform. I am no different. I started building my own websites with pure HTML/CSS/JS and loved it. It was a lot of work. WordPress started in 5/27/03 and my first website spun up in December 2004. I didn’t know about WordPress (WP) until year later. I kept my own website but then started dabbling with it and other CMS platforms.
Because it is so widely used, it is grabs the attention of the hackers of the world. Just like Windows and Chrome. If you have the market majority then you are the platform that people go after.
Over the years my sites have been routinely compromised or attempted at such. I have had to recover much data from backups.
Recently I learned about a username sniffing technique that is used on WordPress to discover usernames so that a brute force attack can be used to gain access to the site backend. I created a lovely redirect to his page from those pesky username sniffs just for fun.
If you type in https://jasrasr.com/?author=1 then you get redirected to https://jasrasr.com/stop-sniffing-me
You could enter any number after the ‘=’ sign. https://jasrasr.com/?author=123 would also redirect to the same: https://jasrasr.com/stop-sniffing-me
That page then is clickable to this page to explain why I did what I did and now I am laughing at the whole thing. I could’ve installed a plugin to block the username sniffs but I like this approach better.
I just tested and created a new test user which makes technically author=2 valid. If this exist then you can see the archives and blog post/pages that were authored by that username. More importantly you can see the username in the URL and on the page.
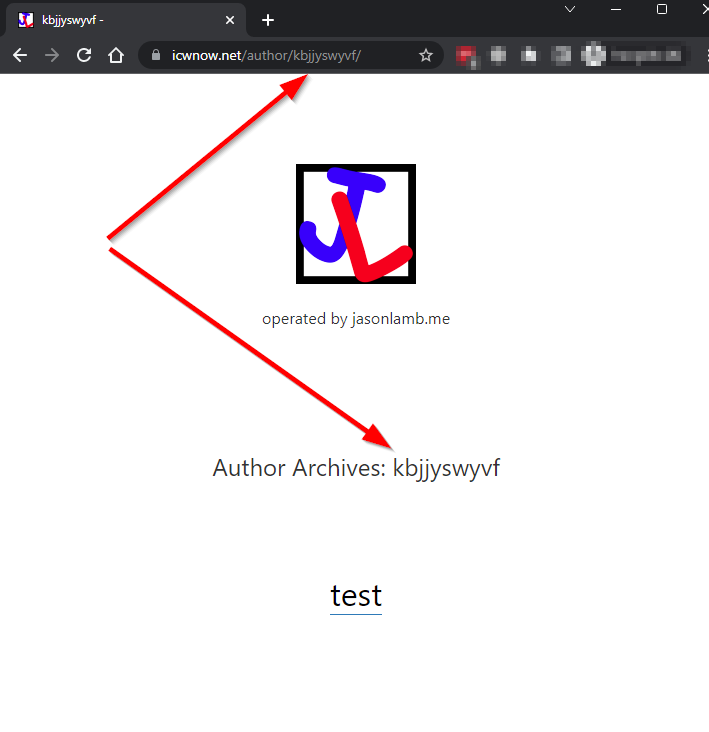
In this example from icwnow.net you can see the username ‘kbjjsywyvf’ and the ‘test’ post that was created. A hacker can take this info and attempt commonly used passwords to gain access to the site.
This page will be updated. I am not done, but it is bed time…
Comments
One response to “Stop Sniffing Me”
-
[…] I know what you’re trying to do. This is not the website you are looking for. […]

You should leave a comment. Jason would like you better if you did. Jason will manually approve all comments before they appear.